Negative effectiveness and deaths. A simplified summary explaining why nobody should take another COVID-19 vaccine.
AlternativeFreePress.com
Part 1 – Negative Effectiveness
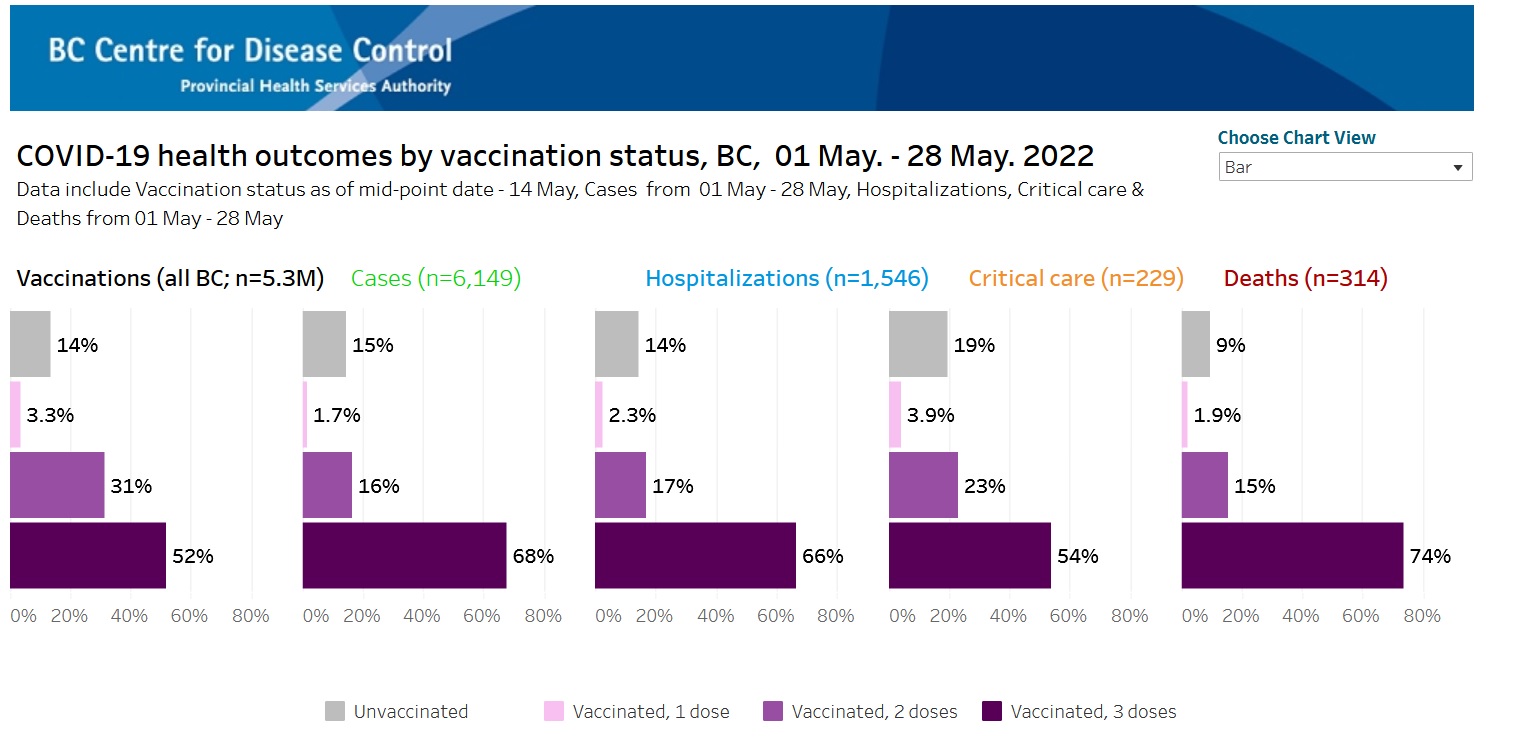
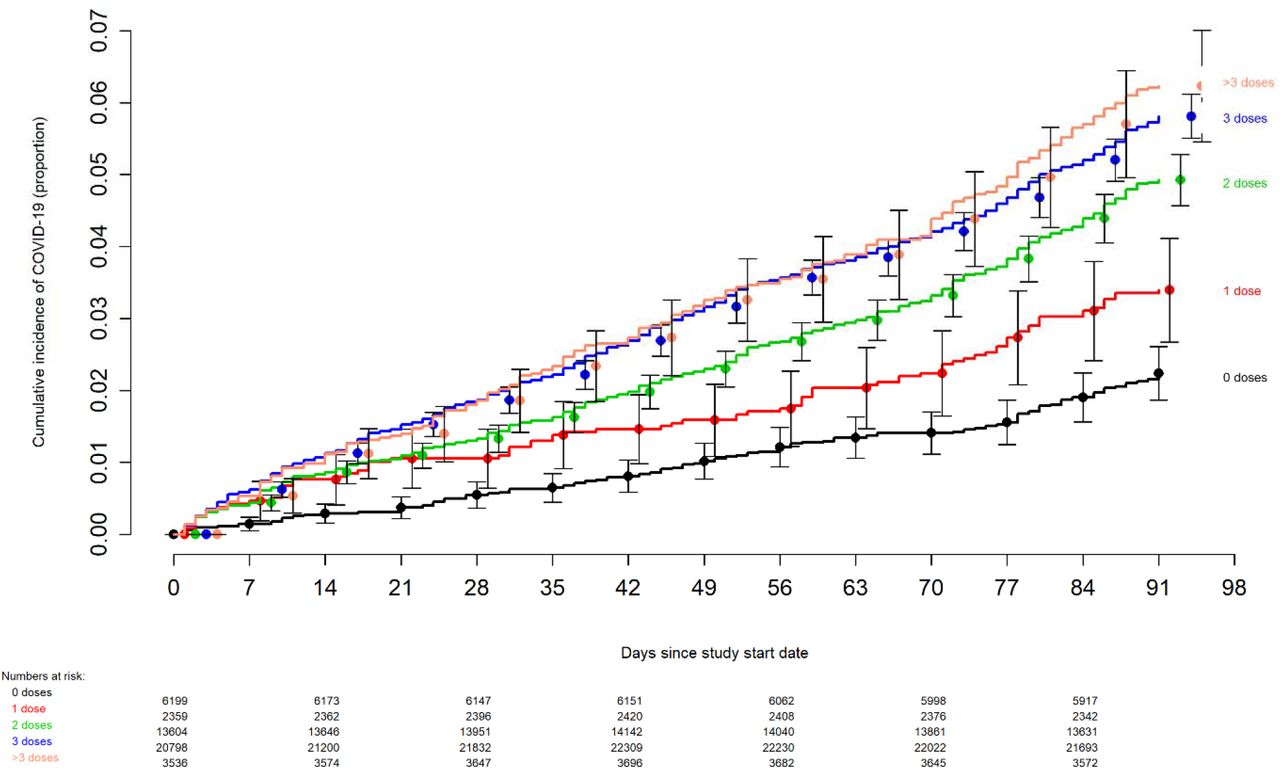
“Effectiveness of the Coronavirus Disease 2019 (COVID-19) Bivalent Vaccine” studied cumulative incidence of COVID-19 among employees at the Cleveland Clinic following vaccination. The following chart shows that as time passed since vaccination, the incidence of COVID-19 infection increased with each dose. The more doses of vaccine, the higher the proportion of COVID-19 infections.
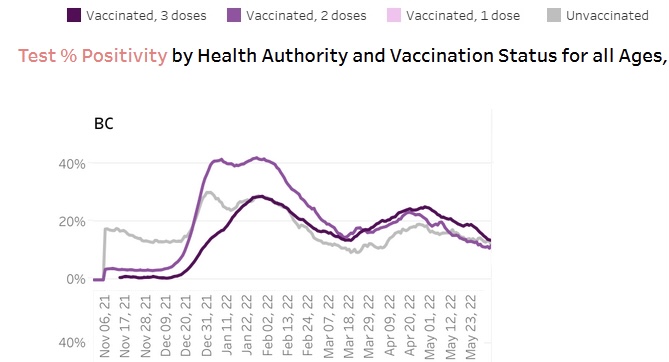
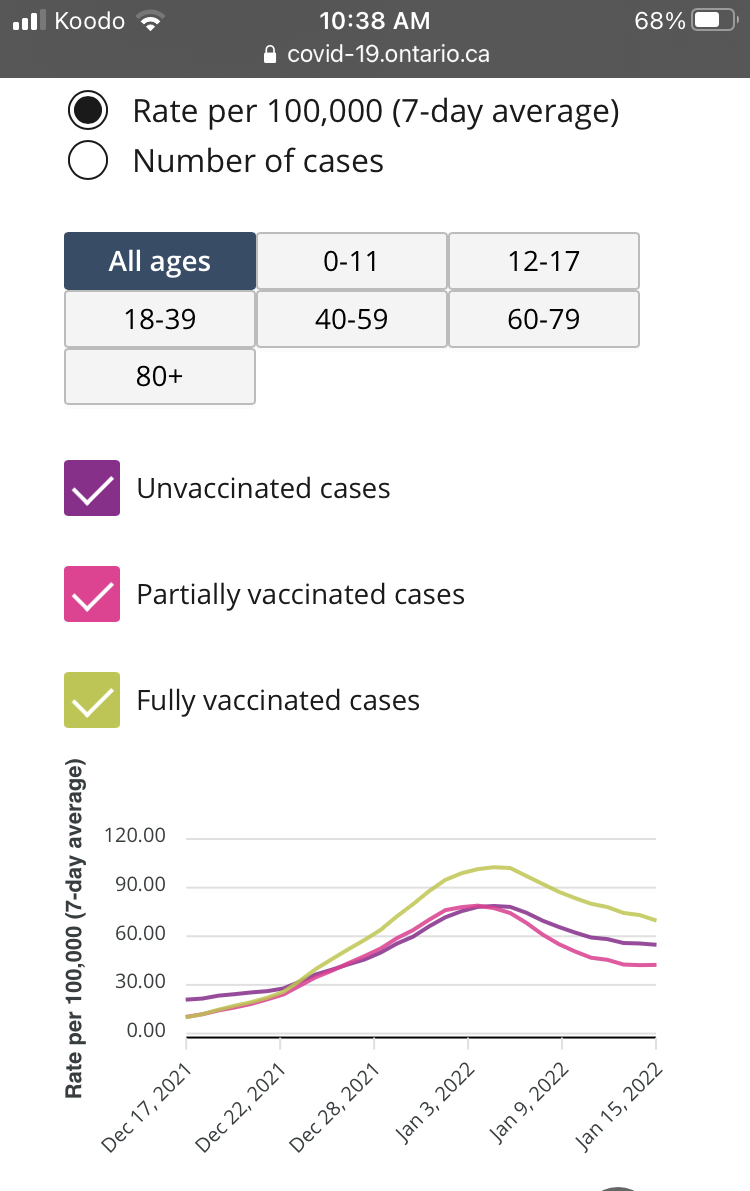
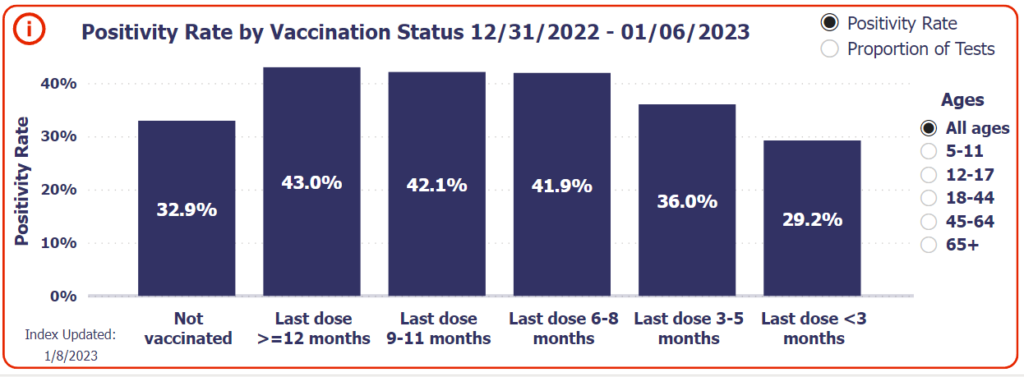
Walgreens has been tracking positivity rate by vaccination status:
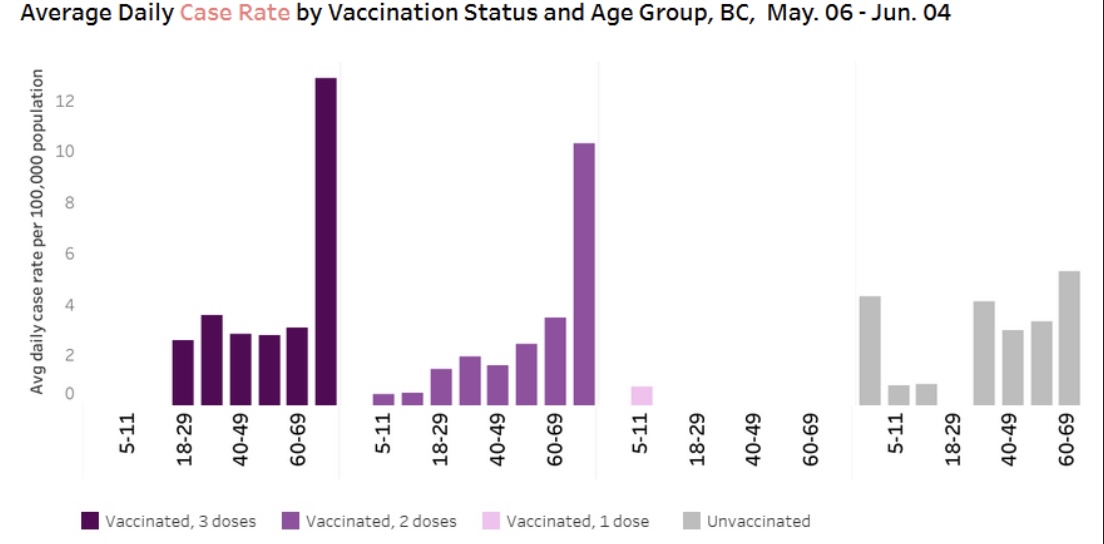
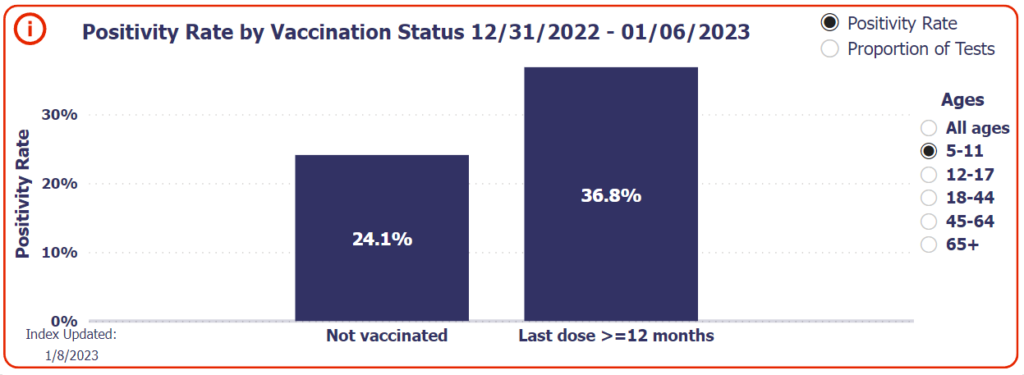
Damning enough on its own, but let’s look at how COVID-19 vaccination impacts infections among children exclusively:
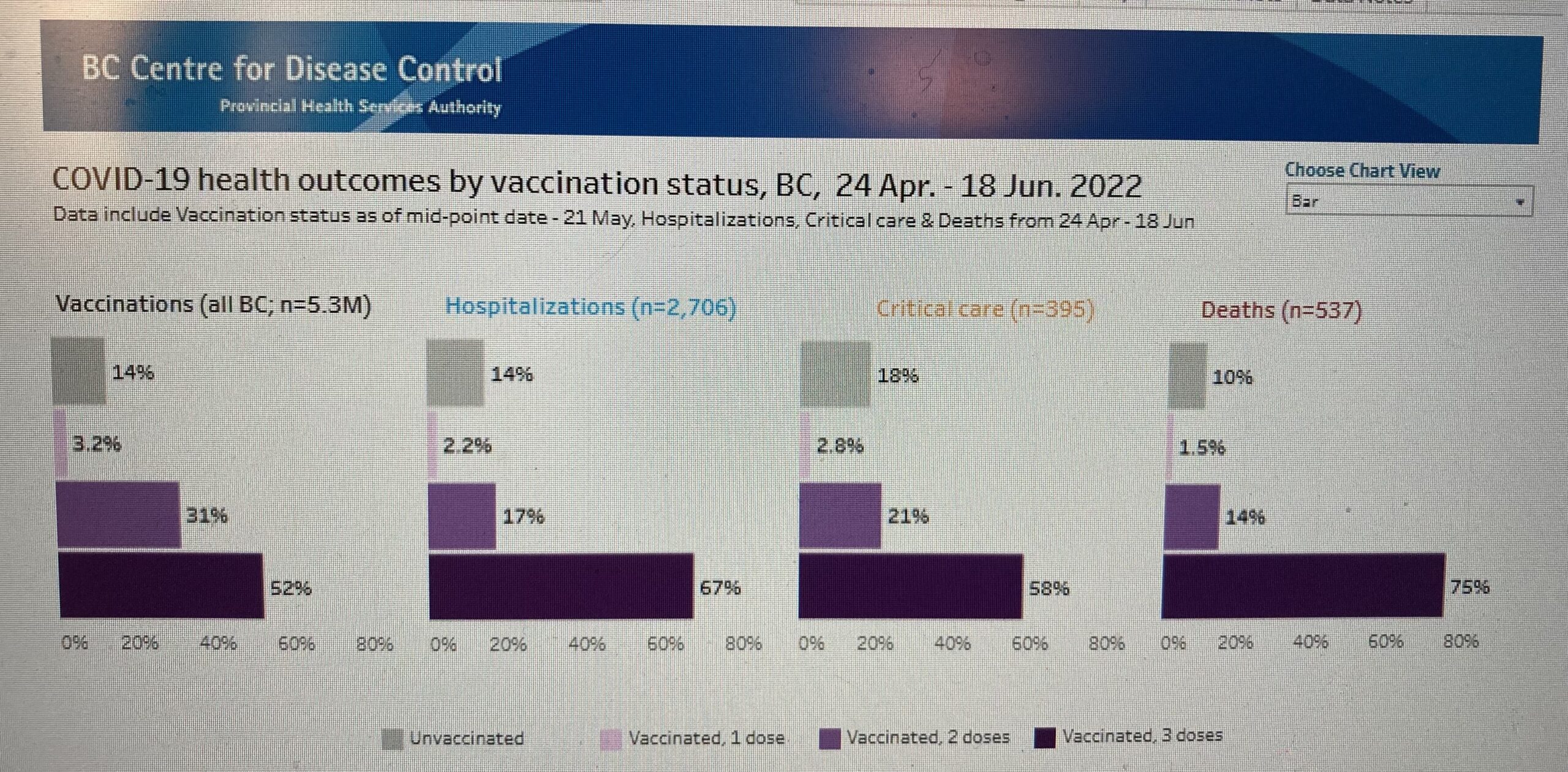
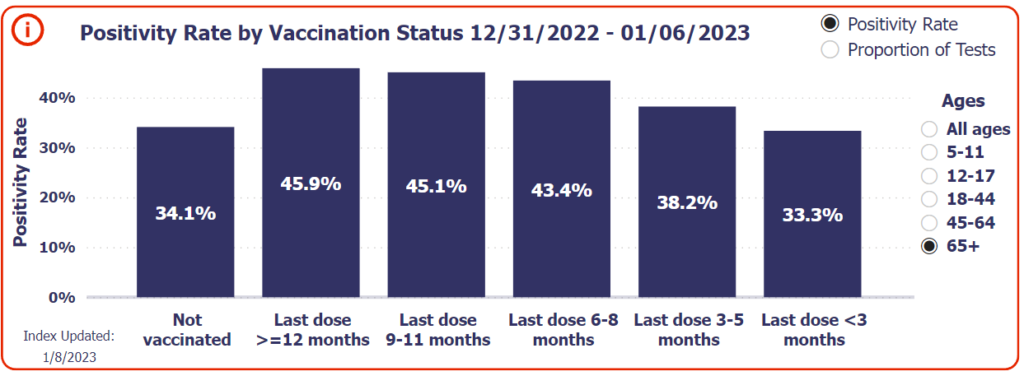
Even the elderly are showing negative effectiveness:
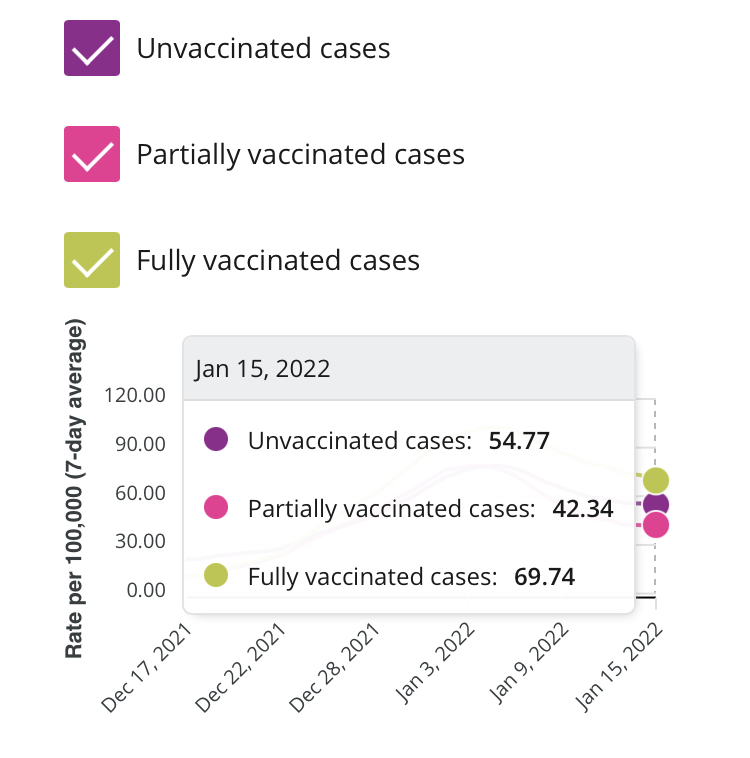
This is consistent with what we have been reporting over the past year in Ontario, BC, Scotland, and more.
Even before the booster, most recipients of either the Pfizer or Moderna vaccines did not have measurable neutralizing antibody titers in serum. Researchers found no increase in efficacy with a second dose.
It is undeniable that the COVID-19 vaccines are not preventing infection, and it seems almost certain that they have increased the infection rate. Let’s look at how….
Part 2 – Antibody Class Switch & Neurodegeneration
The mRNA vaccines encourage the production of IgG4 rather than IgG3, which are not effective at neutralizing pathogens or stimulating an immune response. The body ends up producing far more IgG4 than igG3, which is the opposite of what you would want from a vaccine. IgG3 is 50x better at neutralizing Covid-19. It appears that people are not training their immune systems to fight off Covid-19, instead they seem to be training their body to accept disease progression.
Another new paper confirms that mRNA vaccines “induced long-term IgG4 responses – the IgG subclass with inhibitory effector functions. Furthermore, salivary anti-S IgA levels were lower and decreased faster in naïve as compared to pre-infected vaccinees”
Neurological damage is also a problem associated with the COVID-19 vaccines. Researchers have concluded that “neurodegeneration is in part due to intensity and duration of spike protein exposure, patient age, cellular autophagy activity, and activation, function and regulation of p53. Finally, the neurologically damaging effects can be cumulatively spike-protein dependent, whether exposure is by natural infection or, more substantially, by repeated mRNA vaccination.”
Obviously, neurological damage and a broken immune system which produces the wrong antibodies are things most people want to avoid. However, it does help explain why so many people are dying.
Part 3- Vaccinated COVID-19 Deaths
We have been told that the COVID-19 vaccines prevent death. Unfortunately, data from various governments around the world show that, despite Omicron being a less lethal variant, deaths have only increased since the mass vaccination campaign.
Data from Australia is extremely clear. Almost nobody died from COVID-19 before vaccination. Since vaccination, Australia has seen an explosion of COVID-19 deaths:
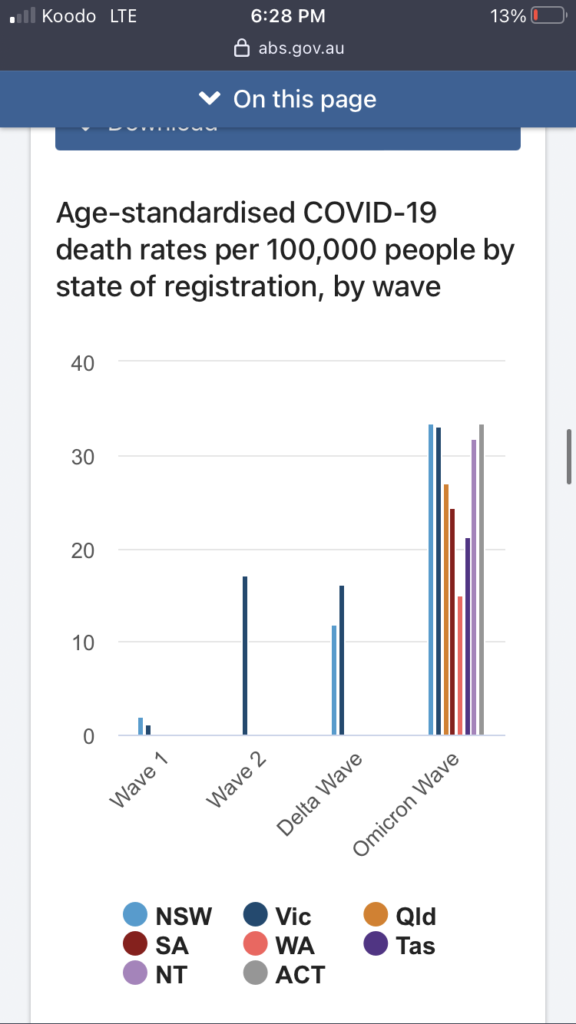
In heavily vaccinated Japan, record number of COVID-19 deaths:

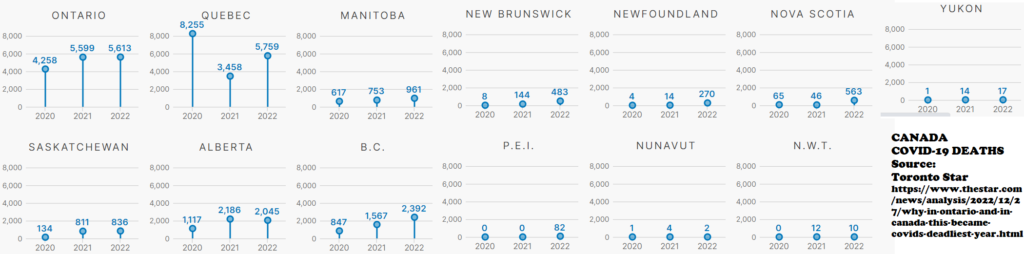
2022 was also the highest number of COVID-19 deaths in Canada:
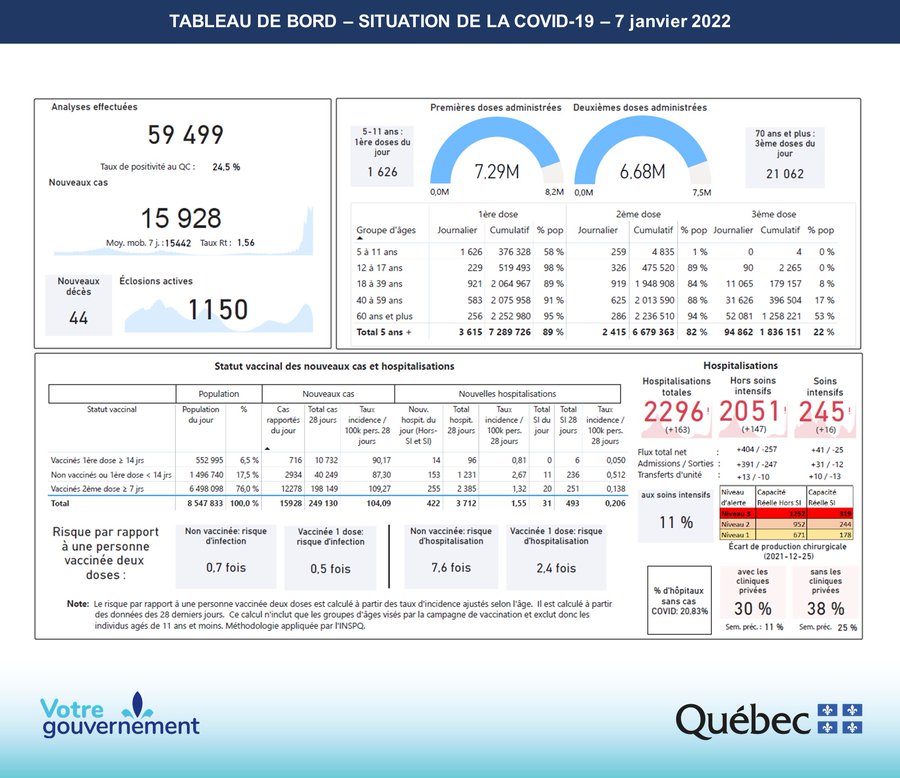
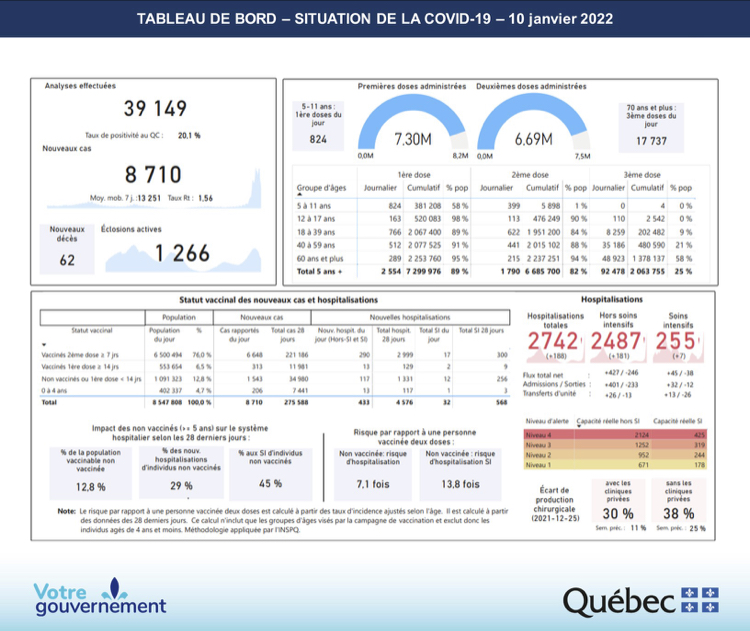
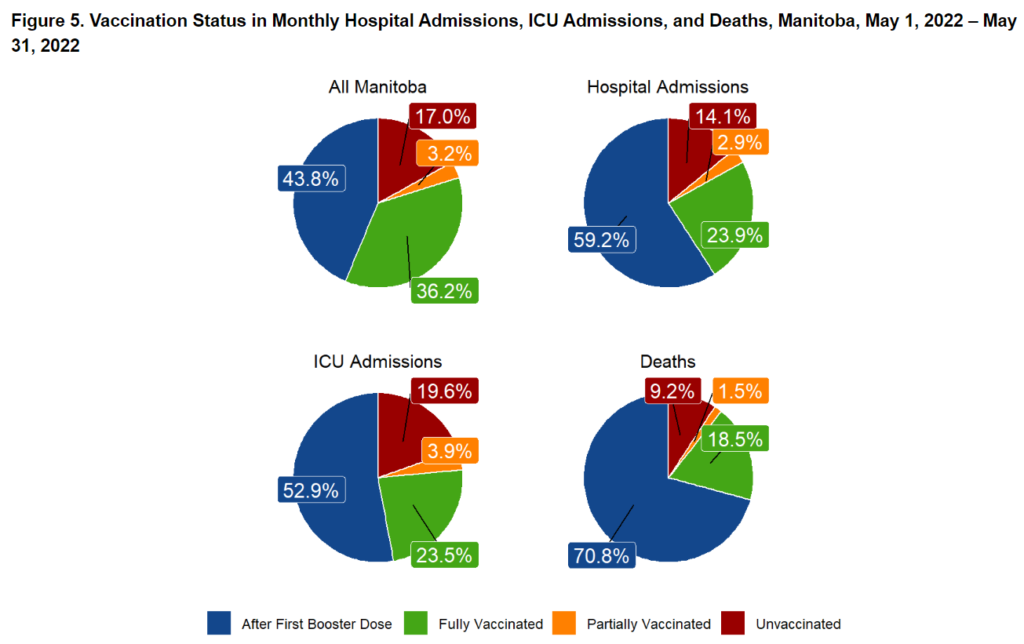
Here is data from Manitoba (2022 week 30 report), it shows a higher rate of death among vaccinated people compared to unvaccinated. The next week they stopped reporting these metrics:
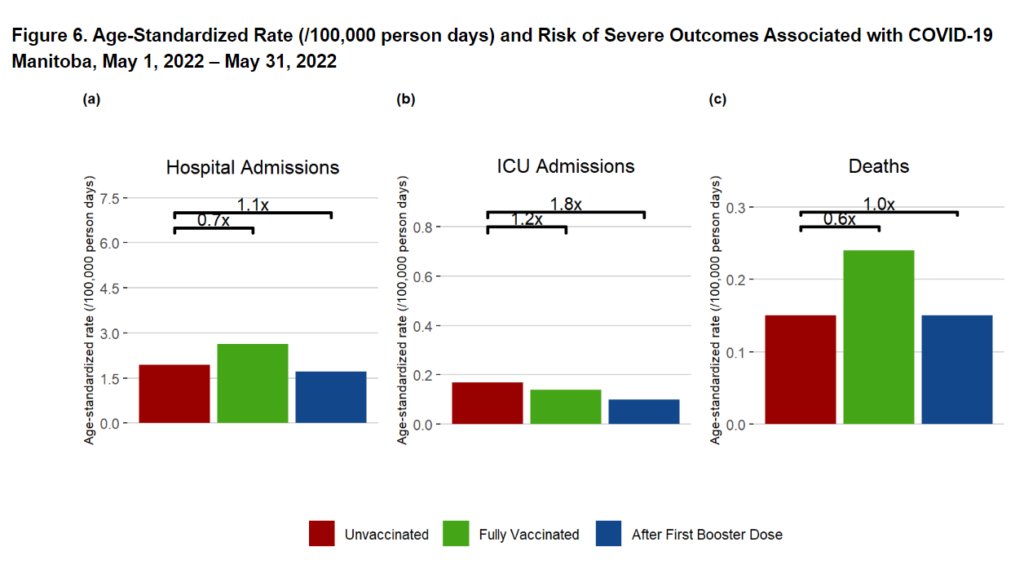
The COVID-19 vaccines are not stopping people from dying of COVID-19. The so called “pandemic of the unvaccinated” has turned out to be quite the opposite with more vaccinated deaths than unvaccinated. Of course, even more people are dying from other causes.
Part 4 – Excess Mortality
In addition to COVID-19 deaths, governments of heavily vaccinated countries around the world have reported excess mortality far exceeding those attributed to COVID-19.
This chart from The Netherlands is especially telling. You can see a huge spike in excess mortality immediately following the start of the vaccination campaign, continued excess mortality throughout 2022, and another spike in excess mortality immediately following the start of the booster campaign.
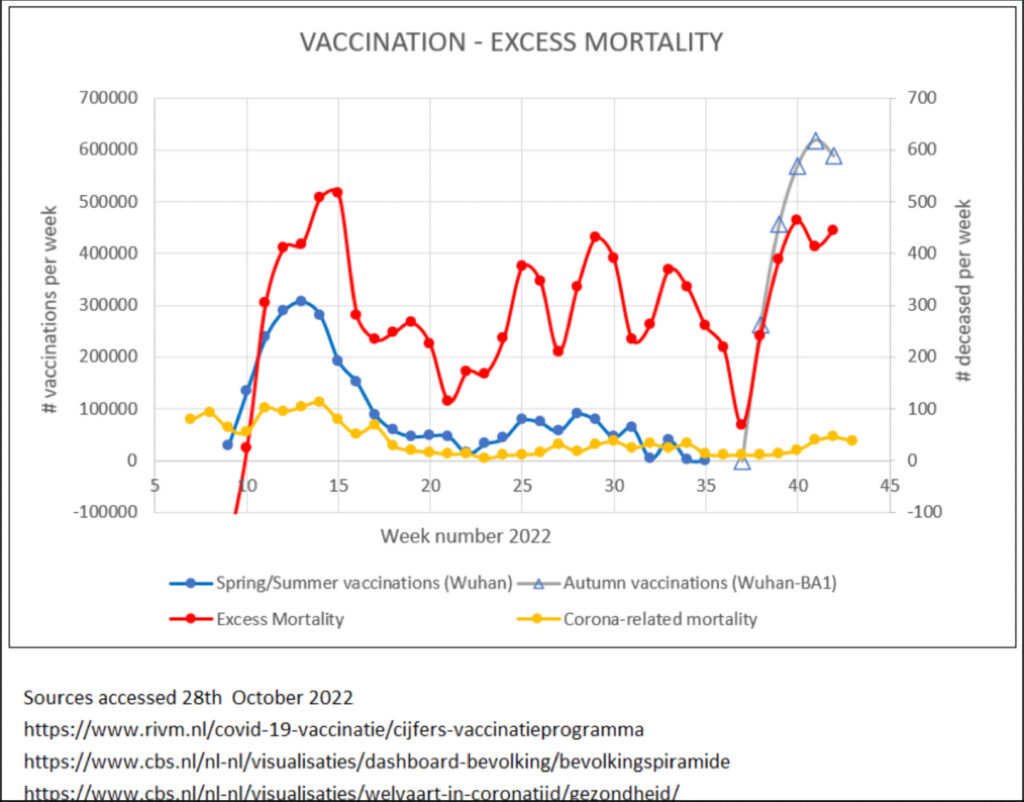
Canada is also experiencing significant excess mortality post-vaccination:
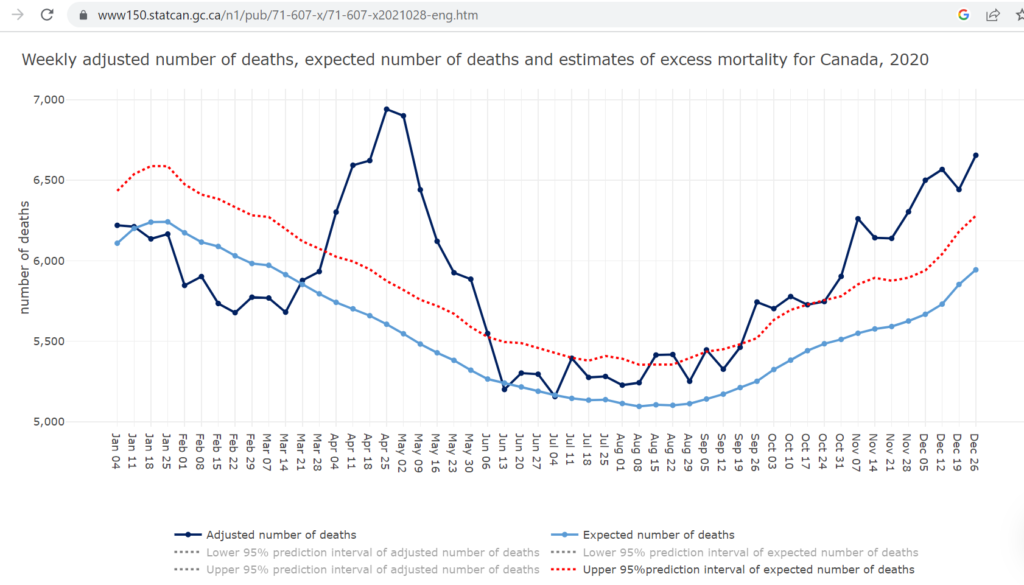
Heavily vaccinated countries around the world are experiencing similar excess mortality to the Netherlands and Canada. What lives are being saved by this vaccination campaign? While we might have extended the lives of some elderly people by a few years, it seems many more young people are falling over dead.
Here is a chart breaking down excess deaths in England. It shows that in the second half of 2022, excess mortality was happening in ALL age categories.

UK data showed that vaccinated are dying at a much higher rate than unvaccinated, so, astonishingly, the UK decided to stop reporting that data.
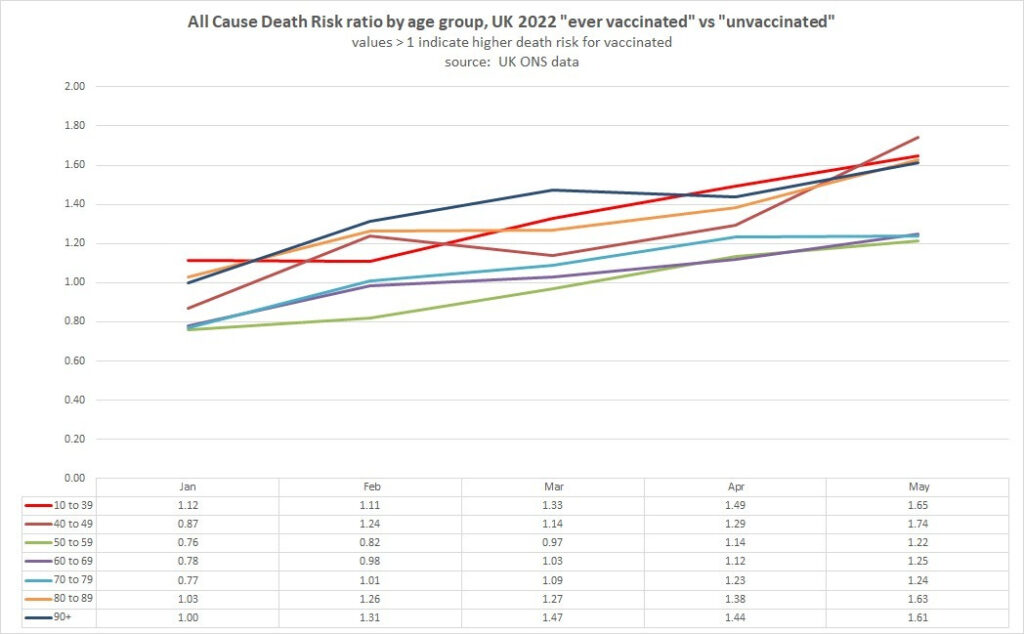
Part 5 – What’s Killing People?
It seems that these vaccines are causing several problems. In addition to homogenizing the human immune response, to a new virus that is rapidly becoming more genetically diverse, there have been numerous reports of both cardiovascular deaths and rapid cancer progression.
According to the Canadian Journal of Cardiology: Mortality rates from cardiovascular diseases have risen more than those of any other non–COVID-19 ailment. And there are many more people and younger people dying from cardiovascular disease than from COVID-19, at any stage of the COVID-19 pandemic. Similar findings come from the UK. Overall, there has been increasing cardiovascular disease mortality worldwide.
“The mRNA vaccines are not safe, not effective and not necessary,” Conservative MP Andrew Bridgen told Parliament last month. “The Government’s current policy on the mRNA vaccines is on the wrong side of medical ethics, is on the wrong side of scientific data, and ultimately it will be on the wrong side of history.”
Cardiologist Dr. Assem Malhotra warns “the mRNA product is a likely contributory factor in all unexpected cardiac arrests, heart attacks, strokes, cardiac arrhythmia & heart failure since 2021 until proven otherwise’”
Watch an interview with Dr Malhotra HERE
Over 17% of teenage vaccine recipients experienced at least one cardiac symptom after the second vaccine dose.
Dr. Peter A McCullough has been warning about the cardiovascular dangers of the COVID-19 vaccines for a year. He has said “The vaccines should be pulled off the market. They clearly are not solving the problem” among many other warnings. He is crystal clear that “they’re not turning out to be safe or effective.”
Watch an interview with Dr. McCullough HERE
Could these cardiovascular events be caused by COVID-19 itself? Recent research says NO: Prior to the vaccine launch, the incidence of myocarditis during the pandemic, apparently decreased by 27% compared with a pre-COVID period of time. Additionally, while it has also been suggested that Covid-19 affects the heart through myocarditis, in a study of 37 fatal COVID-19 cases with 21 controls, replication was not detected in COVID-19 hearts using RNA in situhybridization. On top of that, another study found: “There is not yet definitive EMB/autopsy proof that SARS-CoV-2 causes direct cardiomyocyte damage in association with histological myocarditis. Clinical epidemiology data suggest that myocarditis is uncommon for both SARS-CoV-2-positive and -negative PCR cases.” Finally, to put a nail in the coffin of that persistent misconception, COVID-19-Associated cardiac pathology at the postmortem evaluation: a collaborative systematic review found: “The median reported prevalence of extensive, focal active, and multifocal myocarditis were all 0.0%.”
Of course, this leads us to the question of, why are you reading all this on an obscure blog instead of CNN, MSNBC, or even Facebook?
Part 6 – The Media Cover-up
The Twitter Files proved beyond any doubt that the government colludes with media companies to censor information. While more details are expected to emerge in coming weeks, we have already learned that the US Government was very active suppressing information about COVID-19 and vaccines.
No matter what your opinion about the COVID-19 vaccines, everyone should want transparency and honesty from their media and governments. We now know with absolute certainty that that was not the case with the COVID-19 pandemic.
Why? It could be because the people who authorized emergency approval for these vaccines collect royalties from the sales of those same vaccines. Anthony Fauci believes he should not need to disclose how much he is being paid from vaccine royalties. This is the same person who authorized gain-of-function research which created the virus in the first place, and then proceeded to cover it up.
That said, Fauci wasn’t the only person covering things up.
Part 7 – Fraudulent Trials & Ignored Safety Signals
The FDA has actually been ignoring multiple safety signals. “The fact that the FDA found these four safety signals means they should have followed up on the results and I don’t understand why we haven’t had more information since then. It has been over a year,” says Tracy Høeg, epidemiologist and physician currently conducting covid-19 vaccine research with the Florida Department of Health and California’s Marin County Department of Health and Human Services.
The results of another safety study hidden inside a different study protocol for evaluating boosters by the FDA stated, “In a cohort study of the third dose safety in the Medicare population where historical controls were used, we detected a statistically significant risk for immune thrombocytopenia (incidence rate ratio 1.66, confidence interval 1.17 to 2.29) and acute myocardial infarction (IRR 1.15, CI 1.02 to 1.29) among people with prior covid-19 diagnosis as well as an increased risk of Bell’s palsy (IRR 1.11, CI 1.03 to 1.19) and pulmonary embolism (IRR 1.05, CI 1.0001 to 1.100) in general.”
Whistleblower Brook Jackson documented and reported that an internal audit of the original Pfizer trial was dangerous and violated Federal law. She says that she felt that she had a responsibility to make sure that the participants were protected and that the fraudulent data being collected in the study was not used in any safety and efficacy analysis.
On September 25, 2020, she spoke to an agent at the FDA, and within hours, she was fired by Pfizer.
When the CDC finally looked at VAERS, “There were 770 different types of adverse events that showed safety signals in ages 18+, of which over 500 (or 2/3) had a larger safety signal than myocarditis/pericarditis. CDC analysis shows that the number of serious adverse events reported in less than two years for mRNA COVID-19 vaccines is 5.5 times larger than all serious reports for vaccines given to adults in the US since 2009.”
Recently a leaked video from Israeli Ministry of Health proves with extremely well done research, that the COVID-19 vaccines are unsafe and that serious safety signals have been ignored, that the COVID-19 vaccines cause severe adverse events that do not resolve, and it proves causality.
Watch video of Israel MoH Meeting
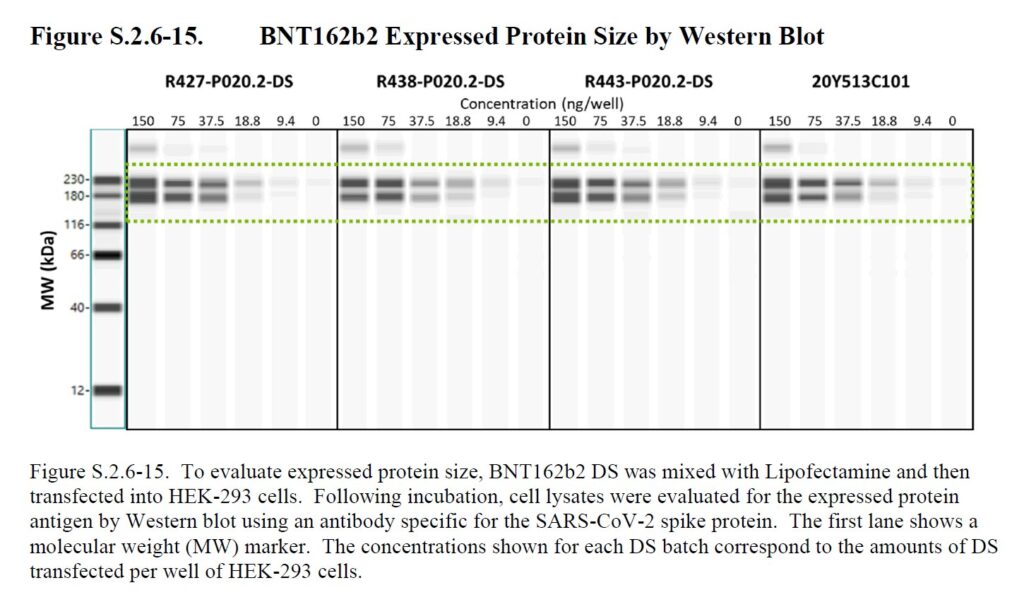
Recently reviewed Pfizer documents contain proof of fraud. The documents contain obviously fake western blots, and it seems regulators failed to even look at the documents Pfizer submitted.
Summary
COVID-19 vaccines are counter-productive at stopping infections. The mRNA vaccines destroy your immune system by causing antibody class switch. They also seem to cause neurological damage, cardiovascular deaths, and rapid cancer progression. Heavily vaccinated countries are experiencing excess mortality, doctors are sounding the alarm, but your government and mainstream media continue to purposefully cover it up.
[JAN 11, 2023 this article has been updated with additional examples of ignored safety signals and fraud]
[JAN 12, 2023 this article was updated with additional evidence that the virus does not cause myocarditis]
[JAN 14, 2023 updated with additional study confirming mRNA vaccines cause class switch and added UK excess death charts]